What Is a Risk Assessment and Why Is It Necessary?
What Is A Risk Assessment?
A Risk Assessment is a comprehensive and exhaustive examination of an organization’s current security controls and information systems. A senior risk assessor works to identify any existing threats or areas of concern, and then provides guidance on how to mitigate the risks identified in the assessment. Risk Assessments are a key part of the Cybersecurity Risk Management Lifecycle.

What Is In A Cybersecurity Risk Assessment?
Risk Assessments analyze all of your organization’s systems, networks, hardware, physical security, and organizational policies to identify potential risks. Once the risks are identified, the assessor then analyzes the risks and evaluates them based on severity. Finally, the assessment concludes with risk treatment options. These treatment options must be acted upon by the organization to improve their cybersecurity maturity. Risk assessments that are not acted upon indicate a critical security flaw in any cybersecurity policy, and left unattended, will leave confidential organizational data exposed to potential cyber-criminal activity. Instead, enact a revolving policy that includes a cycle of quarterly (if not monthly) risk assessments and practical risk treatment strategies.
Why Does My Organization Need to Perform Risk Assessments?
Continuously Changing Attack Surface
With new vulnerabilities being discovered every day it is absolutely critical to continue to evaluate your risk levels and act upon them. Your cybersecurity expert should be aware of all the changes in the attack landscape. If a zero-day vulnerability is located on your systems, you need to be aware of it and employ mitigation strategies immediately. For example, Log4J was a vulnerability in Java that lay undiscovered for 10+ years until late 2021, leaving millions of devices vulnerable to cybercriminal attacks. A patch was introduced to correct the issue, but if an organization was not acting upon cybersecurity risk assessments, they remained unaware of the issue. At least 44% of corporate networks were targeted by cyber criminals by December alone. (checkpoint) Ensure you are employing the Risk Management Lifecycle to give yourself the best protection against cyber events.
Cyber Insurance Policies
Many cyber insurance policies are now requiring risk assessments to purchase and maintain cyber insurance policies. With the rise in ransomware attacks and data breaches, insurance companies are taking a big risk by accepting an organization that does not meet assessment standards. This is expected to increase in popularity, and may soon become a requirement to even apply for cyber insurance.
Regulatory Bodies and Legislation
ISO 27001 6.12: Organizations must establish and maintain an effective Information Security Management System
NIST SP 800-30 Guide for Conducting Risk Assessments: Provides organizations with guidance for conducting risk assessments through three tiers of the risk management hierarchy.
HIPPA Security Rule: The Security Rule protects electronic Personal Health Information (PHI) and gives guidance on how to store, create, receive, and use PHI.
Resources:
https://csrc.nist.gov/projects/risk-management/about-rmf
https://www.itgovernanceusa.com/cyber-security-risk-assessments
https://www.itgovernanceusa.com/iso27001-risk-assessment
https://blog.checkpoint.com/2021/12/14/a-deep-dive-into-a-real-life-log4j-exploitation/
https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-30r1.pdf
https://www.hhs.gov/hipaa/for-professionals/security/index.html
Related Blog Posts
Are Your Credentials on the Web?
Let's Find Out! Step 1: Go to haveibeenpwned.com Step 2: Place Your Email (Never your password) Step 3: Click the “pwned?” button. Step 4: Write down all the sites Step 5: Go to every site and change your passwords This step should be based on prioritization of how...
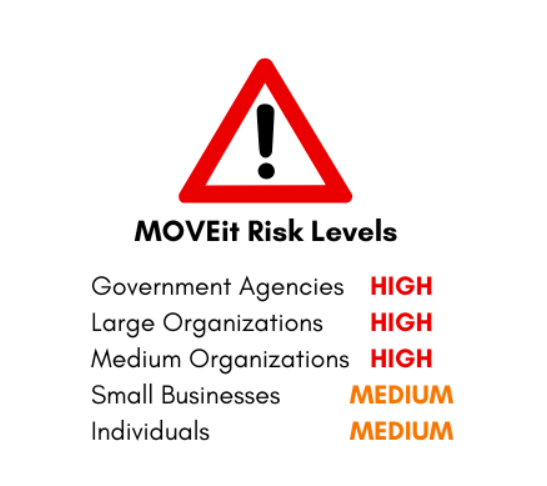
MOVEit: What You Need to Know about CVE-2023-25708
MOVEit: What You Need to Know about CVE-2023-25708 The MOVEit Vulnerability, or CVE-2023-25708, is an SQL Injection vulnerability that targets the database of the MOVEit Transfer software. This is a new critical risk vulnerability and the impacts are...

Madison Horn Joins the Critical Fault Team as CEO
Madison Horn Joins the Critical Fault Team as CEO In Madison’s new role as CEO of Critical Fault, she will lead the vision and strategy for the organization while fostering a culture of growth and collaboration. Madison is dedicated to strengthening...

What Do Hackers Do with Stolen Data
Threat Actors Many individuals may ask, "What would someone want with my data?" or "Who would want my data?" It is important to describe who wants the data because that determines what they are going to do with it. These individuals and organizations...

Newsletter
Subscribe To Our Newsletter
We've been creating some excellent webinars and local events. Join our mailing list for the latest on industry trends and strategies for cyber defense.
Need Immediate Assistance?
Give us a call (405) 771-6399
Headquarters
3841 E Danforth Rd, Ste 106, Edmond, OK 73034
110 E. Houston St, 7th Floor, San Antonio, TX 78205
Copyright 2024 - Critical Fault, LLC. | Privacy Policy


