Penetration Testing Services
What is penetration testing?
Penetration Testing is when an organization hires professional hackers, also known as “ethical hackers”, to identify vulnerabilities in an organization’s security architecture. Once testing is complete, a detailed report is given to the organization identifying risks and vulnerabilities found and providing remediation strategies to help reduce risk of a future cyber event.
Penetration Testing solutions
External Network
Critical Fault’s security experts use Adversary Simulation to assume the role of an outside attacker trying to gain unauthorized access to sensitive organizational data. These tests are used to determine external threats to the organization, including hackers and nation-state attacks.
Mobile device testing
Mobile devices can feature built-in and added security controls, such as mobile device management, passcodes, and encrypted storage. Critical Fault utilizes bleeding edge attacks to test mobile device protections.
Internal Network
Not all threats come from the outside. Employees of an organization also present risks to the security of company networks. These tests are used to determine internal threats to the organization, including insider threat actors and accidental data exposures.
Application Testing
Critical Fault uses D.A.S.T. and S.A.S.T. Penetration testing methods to locate risks and vulnerabilities within a web or mobile application. Our security experts analyze the application in use and dig through the code to find vulnerabilities.
Physical Pentest
Our Red Team tests an organization’s physical security environment by simulating attacks to the company’s buildings, hardware, and remote devices. Physical Pentests identify vulnerabilities in your physical security controls and provide strategies to strengthen those controls.
Social Engineering
Our Red Team utilizes Social Engineering tactics to find weak links in an organization by deceiving employees and tricking them into revealing critical information or allowing access to protected systems.
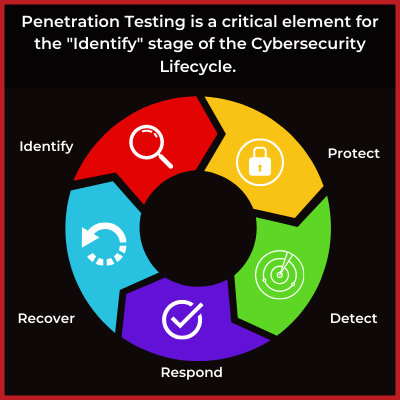
why should i get a penetration test?
Penetration testing has become a critical element to any mature cybersecurity program and is crucial to identifying vulnerabilities that a standard risk assessment or vulnerability scan can miss. 95% of all data breaches are caused by human error. The goal of any penetration test is to find out where these errors are occurring and how to remediate them before a malicious attacker has a chance to exploit them.
Additionally, many regulatory bodies require regular penetration testing to maintain compliance with security standards.

Critical Fault’s Penetration Testing Services are designed to mimic attacks from multiple network perspectives, including rogue admin, guest, and internet hacker. This allows our security experts the ability to identify vulnerabilities that automated scans and systems may miss.
COMMON hacker TARGETS
software
Email servers
network architectures
wireless devices
Computer Systems
Want to learn more? Our Security Experts Are Here For You
Meet Our Red Team
Conoce a Nuestro Equipo Rojo
Kris Wall
CTO, Senior Penetration tester

Jordan Calwell
cSo, Physical security expert
Nick Harris
Penetration tester

Newsletter
Subscribe To Our Newsletter
We've been creating some excellent webinars and local events. Join our mailing list for the latest on industry trends and strategies for cyber defense.
Need Immediate Assistance?
Give us a call (405) 771-6399
Headquarters
3841 E Danforth Rd, Ste 106, Edmond, OK 73034
110 E. Houston St, 7th Floor, San Antonio, TX 78205
Copyright 2024 - Critical Fault, LLC. | Privacy Policy