Servicios de Las Pruebas de Penetración
¿Qué es la prueba de penetración??
Las Pruebas de Penetración ocurren cuando una organización contrata a hackers profesionales, también conocidos como “hackers éticos”, para identificar vulnerabilidades en la estructura de seguridad de la organización. Una vez que las pruebas se completan, se entrega a la organización un informe detallado que identifica los riesgos y vulnerabilidades encontrados y proporciona estrategias para ayudar a reducir el riesgo de un evento cibernético.
¿Por que es necesario las pruebas de penetración?
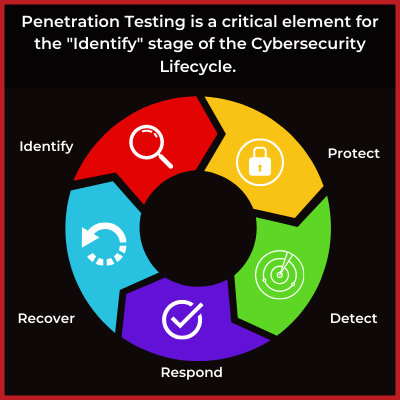
Las pruebas de penetración se han convertido en un elemento crítico para cualquier programa maduro de ciberseguridad. Las pruebas de penetración son cruciales para identificar vulnerabilidades que una evaluación de riesgos estándar o un escaneo de vulnerabilidades puede pasar por alto. El 95% de todas las brechas de datos son causadas por errores humanos. El objetivo de cualquier prueba de penetración es descubrir dónde se están produciendo estos errores y cómo remediarlos antes de que un atacante malintencionado tenga la oportunidad de explotarlos
Además, muchos organismos reguladores exigen pruebas de penetración periódicas para mantener el cumplimiento de los estándares de seguridad.

Critical Fault’s Penetration Testing Services diseñadas para imitar ataques desde múltiples perspectivas de red: Administradors malintencionados, Invitados, Hackers de Internet.
This allows our security experts the ability to identify vulnerabilities that automated scans and systems may miss.
OBJETIVOS COMUNES de Hackers
software
SERVIDORES DE CORREO
ARQUITECTURAS DE REDES
FIREWALLS/CORTAFUEGOS
SISTEMAS INFORMÁTICOS**
Soluciones de Pruebra de Penetration
PRUEBA DE PENETRACIÓN DE RED EXTERNA
Las pruebas de penetración externas apuntan a vulnerabilidades dentro de los sistemas perimetrales de una organización, como aplicaciones web, sitios web, servidores de correo electrónico u otros sistemas accesibles desde Internet. Un profesional de seguridad asume el rol de un atacante externo que intenta obtener acceso no autorizado a datos confidenciales de la organización. Estas pruebas se utilizan para determinar las amenazas externas a la organización.
PRUEBA DE PENETRACIÓN DE RED INTERNA
Not all threats come from the outside. Employees of an organization also present risks to the security of company networks. These tests are used to determine internal threats to the organization, including insider threat actors and accidental data exposures.
PRUEBAS DE PENETRACIÓN FÍSICA
Se prueba un entorno de seguridad física simulando ataques a los edificios, hardware y dispositivos remotos de una organización. Los hackers seguido implementan hardware maligno dentro de una organización violando el perímetro del edificio e insertando un dispositivo infectado en la red de la organización. Critical Fault simula los intentos de un actor de amenazas de violar físicamente el perímetro de la organización mediante ingeniería social, abusando de los controles físicos deficientes o utilizando una variedad de herramientas para obtener acceso no autorizado a áreas y sistemas sensibles.
PRUEBAS DE PENETRACIÓN DE APLICACIONES
Las aplicaciones a menudo dependen de controles de seguridad externos, como cortafuegos de aplicaciones web, y tienen múltiples roles de usuario que requieren pruebas. A menudo, los controles de seguridad internos nativos de la aplicación faltan o, peor aún, no están aprobados. Nuestro Equipo Red probará contra todos los roles y controles de seguridad que protegen las aplicaciones.
Critical Fault utiliza dos Enfoques en Pruebas de Penetración para Aplicaciones
D.A.S.T.
Pruebas de Seguridad de Aplicaciones Dinámicas
Examina la aplicación en tiempo real para encontrar fallas e identificar áreas de riesgo.
S.A.S.T.
Pruebas de Seguridad de Aplicaciones Estáticas
Examina el código fuente para encontrar fallas ocultas en las profundidades de la aplicación
INGENIERIA SOCIAL
A menudo, la forma más fácil de infiltrarse en una organización es a través de los humanos, no de los sistemas. Los hackers saben esto y utilizan errores comunes de los usuarios para infiltrarse en los sistemas organizacionales. Estas tácticas de Ingeniería Social suelen ser muy efectivas. Nuestro Equipo Red utiliza estas tácticas para encontrar puntos débiles en una organización y obtener acceso no autorizado a sistemas e instalaciones seguras mediante el engaño a los empleados y haciéndolos revelar información crítica o permitir el acceso a sistemas protegidos. La Ingeniería Social a menudo se combina con otros compromisos de pruebas de penetración.
What is Penetration Testing?
Penetration testing, or ethical hacking, is an assessment of a company’s current security controls for information systems and buildings by employing the same techniques as real-world hackers to seek out and exploit vulnerabilities that put the confidentiality, availability, or integrity of an organization’s information at risk.
What Types of Penetration Tests Are There?
Penetration testing is typically performed against systems where all security controls are left in place. This helps to identify weaknesses in a system’s security controls.
Network Penetration Testing – a network security environment is tested by simulating real-world hacking techniques to try to bypass security systems and gain unauthorized access to an organization’s systems, networks, applications, or data.
Physical Penetration Testing – a physical security environment is tested by simulating a malicious actor’s attempts to physically breach the organization’s perimeter through social engineering, abusing poor physical controls, or utilizing a variety of tools to gain unauthorized access to sensitive areas and systems.
Application Testing – an application’s architecture, configuration, and design are assessed to identify any vulnerabilities that may put the application and underlying infrastructure at risk of being compromised.
Mobile Application Testing – similar to application testing, a mobile application’s architecture, configuration, and design are assessed to identify any vulnerabilities that may put the application and underlying infrastructure at risk of being compromised.
What is Adversary Simulation?
Adversary Simulation, or Red Teaming, is a process in which expert ethical hackers attempt to breach a security system by using the same techniques as real-world malicious actors, such as hackers. This allows organizations to spot and correct vulnerabilities before an actual attacker has a chance to exploit them.
What is Digital Forensics?
Digital Forensics is a formal process of analysis used by security experts after a security incident has occurred. This process can help the organization perform a root-cause analysis or prepare for potential court proceedings.
What is Incident Response?
Incident Response, often shortened to “IR”, is the immediate protocols and steps an organization and their cybersecurity team takes after an incident has occurred. Incident Response Planning “IRP” is a critical component that should be addressed before an incident has occurred.
What is a Risk Assessment?
A Risk Assessment is a comprehensive and exhaustive examination of an organization’s current security controls and information systems. A senior risk assessing works to identify any existing threats or areas of concern, and providing guidance on how to mitigate the risks identified in the assessment.
What is Threat Modeling?
Threat modeling is a formal process designed to help information security teams identify and prioritize potential threats to information systems.
What is the Average Cost of a Cyber-Attack?
According to IBM Newsroom, in 2021, the average cost per incident was $4.24 million – the highest in 17 years.
What are the Main Types of Cyber-Attack?
Ransomware – Ransomware is unauthorized malicious software that is installed on networked systems, allowing the attacker to encrypt and lock systems until a ransom is paid to the attackers. Payment is typically made through cryptocurrencies, such as Bitcoin.
DDoS – or Distributed Denial of Service attack, is when the attacker tries to make a network system or application inaccessible to its intended users by flooding the system with large amounts of traffic, effectively denying access to legitimate users.
Drive-By Downloads – Drive-By Downloads are unintentional downloads of malicious code due to out-of-date software.
Zero-day – Zero-days are recently discovered vulnerabilities where the vendor hasn’t yet developed a security patch, allowing hackers an opportunity for attack.
MitM Attacks – when an attacker positions himself in between communications and eavesdrops for information or impersonates another individual to gain information.
Phishing Email – Phishing emails are a social engineering attack in which an attacker sends a fake message to an employee asking them to take an action. When the action is made, it helps provide the attacker increased access to systems or sensitive information.
Does My Business Need a Cybersecurity Plan?
Malicious hackers target based on a company’s vulnerability, not necessarily their sensitivity or size. 43% of all cyber-attacks are aimed towards small businesses. Additionally, the number of data breaches and hacking attempts increased by 27% between 2020 and 2021. With cybercrimes reaching an average of $4.24 million dollars in losses per incident, cybersecurity is critical to any business’ survival.
How Can I Reduce Threats?
Ensure you are participating in information security best practices.
Perform regular penetration tests and vulnerability assessments to recognize and mitigate vulnerabilities before they become a problem.
Train your employees on social engineering attempts and how to protect themselves.
Practice separation of duties between employees to ensure work is being double checked for integrity.
Ensure your physical infrastructure is properly protecting sensitive hardware, data storage, and company information from unauthorized access.
What is a Vulnerability Assessment?
A systematic review of an organization’s information system assets, including security controls and networks, with the intent of identifying vulnerabilities and areas of improvement while giving recommendations on remediation of those vulnerabilities.
What is the Difference Between a Vulnerability Assessment and a Penetration Test?
Vulnerability assessments are high-level tests that scans security systems and reports any vulnerabilities found. These assessments are often automated and tend to ignore the human element of a potential breach. Vulnerability scanners search for known vulnerabilities but are unable to identify previously undiscovered vulnerabilities.
A penetration test is performed by a certified penetration tester to actively exploit known and unknown vulnerabilities and determine an organization’s risk level. Penetration testing uses a thorough real-world approach to finding vulnerabilities and determining the severity of those weaknesses.
Why Do We Perform Penetration Testing?
Vulnerability assessments cannot predict human behavior. 95% of all cybercrime is caused by human error. Penetration testing allows for exploitation of human error and identifies vulnerability within the organization’s processes, structures, and infrastructure, as well as their security systems. Vulnerability assessments and penetration testing should both be performed routinely and remediation efforts should always be acted upon.
How Often Should I Be Conducting Penetration Testing?
Penetration testing should be conducted regularly, at least once a year, if not quarterly depending on the company’s risk levels, sensitivity, or regulatory standards.
How Often Should I Be Conducting Vulnerability Assessments?
Want to learn more? Our Security Experts Are Here For You
Meet Our Red Team
Conoce a Nuestro Equipo Rojo
Kris Wall
CTO, Senior Penetration tester

Jordan Calwell
cSo, Physical security expert
Nick Harris
Penetration tester

Newsletter
Subscribe To Our Newsletter
We've been creating some excellent webinars and local events. Join our mailing list for the latest on industry trends and strategies for cyber defense.
Need Immediate Assistance?
Give us a call (405) 771-6399
Headquarters
3841 E Danforth Rd, Ste 106, Edmond, OK 73034
110 E. Houston St, 7th Floor, San Antonio, TX 78205
Copyright 2024 - Critical Fault, LLC. | Privacy Policy