MOVEit: What You Need to Know about CVE-2023-25708
MOVEit: What You Need to Know about CVE-2023-25708
The MOVEit Vulnerability, or CVE-2023-25708, is an SQL Injection vulnerability that targets the database of the MOVEit Transfer software. This is a new critical risk vulnerability and the impacts are becoming more widespread as more information is discovered. This attack affects all previous versions of MOVEit Transfer including:
- MOVEit Transfer 2023.0.x
- MOVEit Transfer 2022.1.x
- MOVEit Transfer 2022.0.x
- MOVEit Transfer 2021.1.x
- MOVEit Transfer 2021.0.x
Background
MOVEit is a secure file transfer software created by Progress. It is widely used in North America and Europe by government agencies and large corporations to easily share files between organizations and individuals. MOVEit Transfer allows for files to be encrypted both at rest and in transit, making this software widely used and trusted for data transfer that contains sensitive information.
SQL injections utilize the target web application’s search query to gain unauthorized access to sensitive systems and privilege escalation. Using CVE-2023-25708, the attacker has the ability to create, modify, or destroy user profiles and data. Threat actors around the globe are actively exploiting this zero-day vulnerability before patches are applied. The attacker can access the security architecture and begin to elevate privileges. Once in, the hacker has the ability to start installing programs, altering or destroying data, or creating unauthorized users. This has the highest impact on organizations who have large numbers of employees and customers accessing and using MOVEit Transfer. Therefore, it is critical that any organization that may be impacted by this attack take immediate steps to safeguard their organization and data.
What is the Impact of MOVEit?
There is no indication that this is a targeted attack against specific corporations. Threat actors are using the CVE-2023-25708 vulnerability as an opportunity to access and steal data. CL0P, a Russian ransomware gang known for asking for multimillion dollar ransoms, is actively exploiting this vulnerability and has already released an incomplete list of organizations affected. CL0P announced recently that any stolen government data will be destroyed. The US Department of State, along with the FBI and CISA, is offering a reward for any information regarding CL0P and the MOVEit vulnerability.
CL0P has admitted to ransomware attacks through the deployment of web shell Lemurloot and immediate data theft using CVE-2023-25708. According to cybersecurity watch-dogs, Lemurloot was created specifically to target MOVEit Transit.
From Mandiant:
“LEMURLOOT provides functionality tailored to execute on a system running MOVEit Transfer software, including the ability to generate commands to enumerate files and folders, retrieve configuration information, and create or delete a user with a hard-coded name. Initial analysis suggests that the LEMURLOOT web shell is being used to steal data previously uploaded by the users of individual MOVEit Transfer systems.”
CVE-2023-25708 and Lemurloot also have the ability to access and copy Azure Blob files and credentials, indicating that attackers may also be stealing data stored in Azure. It is unclear what the full scope of this unauthorized access is, and the impacts of the MOVEit vulnerability on Azure will not be known for some time.
When was it Discovered and What is the Risk Level?
The MOVEit SQL injection vulnerability became public on June 15th, 2023. CVE-2023-25708 is the third vulnerability to hit MOVEit in less than a month. The first vulnerability dates back to May 27th 2023 with CVE-2023-34362, followed shortly by CVE-2023-35708.
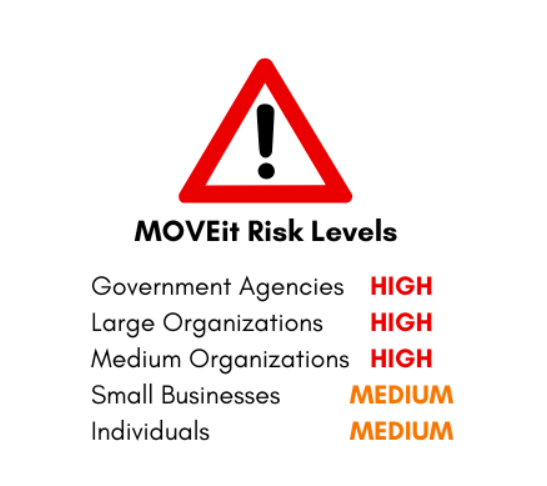
NIST has rated the MOVEit Vulnerability as a rating of 9.8 critical risk on the vulnerability scoring system. This latest attack has a high risk rating for government agencies, a high risk rating for medium-large corporations, and a medium risk to small-medium corporations. Because this is a zero-day vulnerability, the full scope of the attack will not be known for some time. It is imperative to take action now for your organization to protect your agency against possible exploitation.
Who Has Been Impacted?
So far several North American and European companies have come forward to announce that they have been impacted by the MOVEit attack. Some of the larger organizations compromised include:
- US Department of Energy
- Shell
- Oregon Department of Transportation
- Louisiana Office of Motor Vehicles
- Zellis – Canadian Payroll Company
- The BBC
- British Airways
- Boots – UK Retailer
At least 6 million Americans between the Louisiana Office of Motor Vehicles and the Oregon Department of Transportation have had their data exposed to hackers, including driver’s licenses, vehicle registration, social security numbers and addresses. Both states have issued statements warning citizens to freeze their credit and monitor their accounts for suspicious activity. A full list of precautions for individuals to take can be found on the Office of the Governor of Louisiana’s website.
A Federal class action lawsuit was filed recently for the victims of the MOVEit attack. According to Bloomberg, “Progress Software Corp. failed in its duty to protect sensitive information in connection with a data breach of the MOVEit cloud-hosting and file-transfer services it provides to government agencies and private companies…” Progress Software has stated they are unable to comment on an ongoing case but they are committed to helping those affected by the data breach.
If you think your organization has been impacted, click here to find out more about Digital Forensics and how it can help your agency.
How to guard against MOVEit
See here for a full list of CIS Recommendations.
See here for the Progress Community.
Threat actors often use zero-day opportunities before patches are applied and before the news gets much traction. The faster you act against this vulnerability the better chance of keeping your data safe.
- Disable all HTTP and HTTPS access to the MOVEit Transfer environment.
- Immediately apply the 06/15/2023 patch from Progress and update the software.
- Test systems for indicators of compromise using Penetration Testing, Risk Assessments, and Vulnerability Scanners
Even if your organization does not use MOVEit, it is still extremely important to keep up to date with scans, assessments, and penetration testing. Organizations should constantly be assessing and reassessing their security architectures. Threat actors often prey upon organizations that are lax in their security standards and they rely on the opportunities presented by large vulnerabilities such as MOVEit to strike. These attacks are unpredictable and designed to infiltrate the weakest architectures first. Make sure yours is safeguarded.
If you aren’t sure what steps to take next, contact us for a consultation of the impact of MOVEit on your firm.
RESOURCES
- Bloomberg:https://news.bloomberglaw.com/class-action/progress-software-hit-with-class-action-over-moveit-data-breach
- CIS:https://www.cisecurity.org/advisory/a-vulnerability-in-moveit-transfer-could-allow-for-elevated-privileges-and-unauthorized-access_2023-064#:~:text=The%20vulnerability%20is%20an%20SQL,been%20released%20at%20this%20time
- CISA:https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-158a
- CyberNews: https://cybernews.com/news/cl0p-moveit-ransom-attack-victims-names/
- Help Net Security: https://www.helpnetsecurity.com/2023/06/19/cve-2023-35708/
- Mandiant: https://www.mandiant.com/resources/blog/zero-day-moveit-data-theft
- NIST: https://nvd.nist.gov/vuln/detail/CVE-2023-35708
- Office of the Governor of Louisiana: https://gov.louisiana.gov/index.cfm/newsroom/detail/4158
- Progress Community: https://community.progress.com/s/article/MOVEit-Transfer-Critical-Vulnerability-15June2023
- Symantec: https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/moveit-vulnerabilities-exploits
- Tech Radar: https://www.techradar.com/pro/dmv-data-on-millions-of-americans-leaked-make-sure-you-arent-affected-in-latest-moveit-breach
Related Blog Posts
How to Remove Metadata from Word Documents
What is Metadata? According to Britannica: Metadata, data about informational aspects of other data. For example, the date and time of a text message is metadata, but the text of that message is not. The term metadata is a portmanteau of data and meta- (in the word’s...
Are Your Credentials on the Web?
Let's Find Out! Step 1: Go to haveibeenpwned.com Step 2: Place Your Email (Never your password) Step 3: Click the “pwned?” button. Step 4: Write down all the sites Step 5: Go to every site and change your passwords This step should be based on prioritization of how...

Madison Horn Joins the Critical Fault Team as CEO
Madison Horn Joins the Critical Fault Team as CEO In Madison’s new role as CEO of Critical Fault, she will lead the vision and strategy for the organization while fostering a culture of growth and collaboration. Madison is dedicated to strengthening...

What Do Hackers Do with Stolen Data
Threat Actors Many individuals may ask, "What would someone want with my data?" or "Who would want my data?" It is important to describe who wants the data because that determines what they are going to do with it. These individuals and organizations...
Want to learn more? Our Security Experts Are Here For You

Newsletter
Subscribe To Our Newsletter
We've been creating some excellent webinars and local events. Join our mailing list for the latest on industry trends and strategies for cyber defense.
Need Immediate Assistance?
Give us a call (405) 771-6399
Headquarters
3841 E Danforth Rd, Ste 106, Edmond, OK 73034
110 E. Houston St, 7th Floor, San Antonio, TX 78205
Copyright 2024 - Critical Fault, LLC. | Privacy Policy