The Rising Need for Digital Forensics
What is Digital Forensics?
According to US-CERT, Digital (Computer) Forensics can be defined “as the discipline that combines elements of law and computer science to collect and analyze data from computer systems, networks, wireless communications, and storage devices in a way that is admissible as evidence in a court of law.”[1] Digital forensics primarily deals with the process of collecting, analyzing, and documenting latent digital evidence. Digital forensics is a branch of forensic science and is often employed when digital evidence needs to be preserved for legal purposes.

Why is it necessary?
Having a Digital Forensic solution is an essential part of any enterprises’ cybersecurity program. Digital Forensics is a key pillar in the “Defense-in-Depth” approach to information security. Understanding the legal and technical aspects of computer forensics will help you capture vital information if your network/infrastructure is compromised and will assist in the prosecution of the responsible entities.
What’s the difference between incident response and digital forensics?
Digital Forensics can drive and augment incident response. Incident response efforts often leverage intelligent tools (e.g. Indicators of Compromise, signature rules, etc.) and are effective only when there is prior information about the vulnerabilities and mechanisms utilized in an attack. The effectiveness of these tools is inverse to the quantity of new and novel attack techniques and mechanisms utilized by threat actors. Digital forensic processes does not suffer from such issues, and can greatly improve and organizations resiliency and ability to recover from a cyber-incident. Additionally traditional IR efforts do not often preserve evidence in a fashion that would be admissible in a court setting.
What is eDiscovery?
Electronic discovery (eDiscovery) is a term referring to discovery process in legal proceedings. eDiscovery differs from traditional Discovery in that the information in question is in electronic/digital format (also known as ESI). Electronic discovery is dictated by rules of civil procedure and accomplished through formalized processes. Electronic information differs from paper information in various ways (intangible form, transient nature, persistence, etc.). and is usually accompanied by metadata (the preservation of which presents specific challenges)– and is of critical consideration when presenting digital information as evidence.
What is the Chain of Custody?
In Digital Forensics, the Chain of Custody is a process that documents the specifics of evidence collection (including the safeguarding, and analysis throughout its lifecycle) by notating each individual involved in the handling of evidence, when it was collected/transferred, and why it was collected/transferred.
Who is qualified to perform digital forensics?
A qualified digital forensic assessor must be proficient in multiple different domains of technical and administrative knowledge, this includes (but it not limited to) computer science, information assurance, information security, document control and review, metadata analysis, volatile memory extraction, etc.
Related Blog Posts
Are Your Credentials on the Web?
Let's Find Out! Step 1: Go to haveibeenpwned.com Step 2: Place Your Email (Never your password) Step 3: Click the “pwned?” button. Step 4: Write down all the sites Step 5: Go to every site and change your passwords This step should be based on prioritization of how...
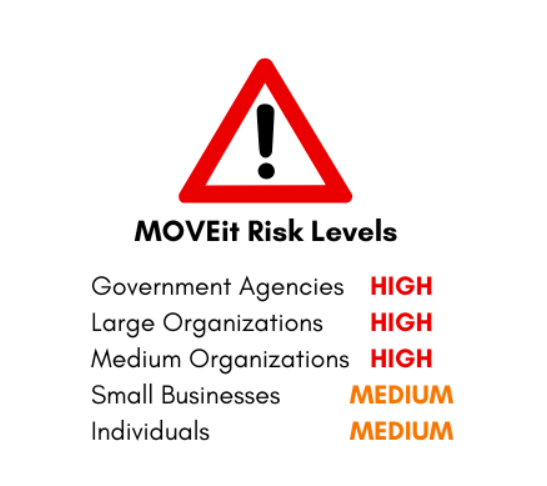
MOVEit: What You Need to Know about CVE-2023-25708
MOVEit: What You Need to Know about CVE-2023-25708 The MOVEit Vulnerability, or CVE-2023-25708, is an SQL Injection vulnerability that targets the database of the MOVEit Transfer software. This is a new critical risk vulnerability and the impacts are...

Madison Horn Joins the Critical Fault Team as CEO
Madison Horn Joins the Critical Fault Team as CEO In Madison’s new role as CEO of Critical Fault, she will lead the vision and strategy for the organization while fostering a culture of growth and collaboration. Madison is dedicated to strengthening...

What Do Hackers Do with Stolen Data
Threat Actors Many individuals may ask, "What would someone want with my data?" or "Who would want my data?" It is important to describe who wants the data because that determines what they are going to do with it. These individuals and organizations...

Newsletter
Subscribe To Our Newsletter
We've been creating some excellent webinars and local events. Join our mailing list for the latest on industry trends and strategies for cyber defense.
Need Immediate Assistance?
Give us a call (405) 771-6399
Headquarters
3841 E Danforth Rd, Ste 106, Edmond, OK 73034
110 E. Houston St, 7th Floor, San Antonio, TX 78205
Copyright 2024 - Critical Fault, LLC. | Privacy Policy


