Recent Blog Posts
What to Expect for CMMC 2.0 Assessments
What to Expect for CMMC 2.0 Assessments So now you have put in all the work to meet the requirements of CMMC 2.0 level 1, 2, or 3, but what’s next? Once the rules are finalized and being implemented, companies will need to be able to certify that they are...
CMMC 2.0 Requirements: Level Three
CMMC Requirements: Level Three Now we enter the most nebulous category of CMMC 2.0 requirements: level three. While we know where the requirements will come from, we don’t know exactly how many will be added from the NIST 800-172 publication. While there are...
CMMC 2.0 Level 2 Requirements
CMMC 2.0 Level 2 CMMC 2.0 Level 2-that’s where things really start to get serious. While the controls required aren’t incredibly difficult, there are probably a fair number that most companies haven’t considered before, especially since there are 110 of them. And I am...
CMMC 2.0 Level 1 Requirements
We’re going to start digging through the CMMC levels, starting with CMMC 2.0 Level 1. I will go through the different protection areas and briefly describe what they mean. I don’t intend for this to be a complete guidance, but more an introduction to allow you to be...
The Levels of CMMC 2.0 Compliance
Previously, we covered a brief history of the Cybersecurity Model Maturity Certification (CMMC 2.0 Levels) and touched on a few details of what it actually is. For this entry, we will be getting deeper into the internals of CMMC to begin breaking it down into its...
What is CMMC 2.0?
At this point, especially if you ever have contracted or subcontracted with the Federal government, you have probably at least heard the letters CMMC thrown about. There may have even been a twinge of trepidation surrounding the letters. But what do these letters...
Crypto Scams and What to Look For
First, standard disclaimer that this post is opinion and we are not licensed financial professionals, nor is anything meant to be taken as official financial advice. However, we have both direct and indirect experience with cryptocurrency and would like to share our...
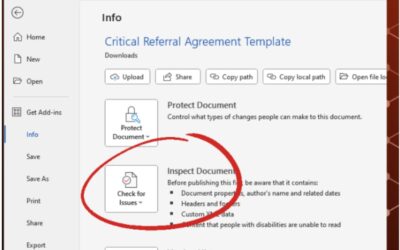
How to Remove Metadata from Word Documents
What is Metadata? According to Britannica: Metadata, data about informational aspects of other data. For example, the date and time of a text message is metadata, but the text of that message is not. The term metadata is a portmanteau of data and meta- (in the word’s...
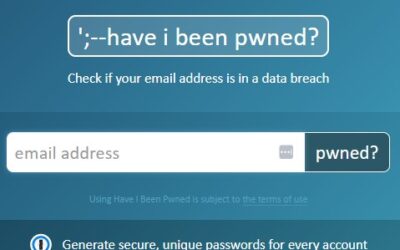
Are Your Credentials on the Web?
Let's Find Out! Step 1: Go to haveibeenpwned.com Step 2: Place Your Email (Never your password) Step 3: Click the “pwned?” button. Step 4: Write down all the sites Step 5: Go to every site and change your passwords This step should be based on prioritization of how...
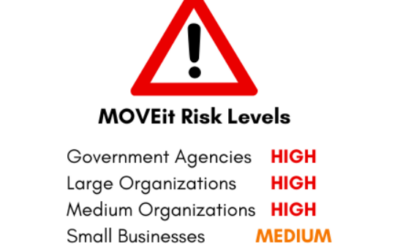
MOVEit: What You Need to Know about CVE-2023-25708
MOVEit: What You Need to Know about CVE-2023-25708 The MOVEit Vulnerability, or CVE-2023-25708, is an SQL Injection vulnerability that targets the database of the MOVEit Transfer software. This is a new critical risk vulnerability and the impacts are...
Madison Horn Joins the Critical Fault Team as CEO
Madison Horn Joins the Critical Fault Team as CEO In Madison’s new role as CEO of Critical Fault, she will lead the vision and strategy for the organization while fostering a culture of growth and collaboration. Madison is dedicated to strengthening...
What Do Hackers Do with Stolen Data
Threat Actors Many individuals may ask, "What would someone want with my data?" or "Who would want my data?" It is important to describe who wants the data because that determines what they are going to do with it. These individuals and organizations...
The Importance of Employee Security Training
Impact of Employee Security Training The majority of enterprise cybersecurity incidents can be traced back to a mistake made by an employee. Whether this came in the form of a clicking on a phishing email or lackluster security policies implemented...
25 High Profile Enterprise Information Security Breaches
No Industry seems to be safe from Ransomeware Thus many sectors have implemented required governance and awareness training throughout their organizations. As time moves forward, more industries will implement proactive strategies to minimize the...
Creating an Incident Response Plan
Creating an Incident Response Plan Disruptions to business operations occur frequently and vary greatly in terms of scope and scale. Organizations should establish formal policies and procedures in order to minimize the impact of...

Newsletter
Subscribe To Our Newsletter
We've been creating some excellent webinars and local events. Join our mailing list for the latest on industry trends and strategies for cyber defense.
Need Immediate Assistance?
Give us a call (405) 771-6399
Headquarters
3841 E Danforth Rd, Ste 106, Edmond, OK 73034
110 E. Houston St, 7th Floor, San Antonio, TX 78205
Copyright 2024 - Critical Fault, LLC. | Privacy Policy