Creating an Incident Response Plan
Creating an Incident Response Plan
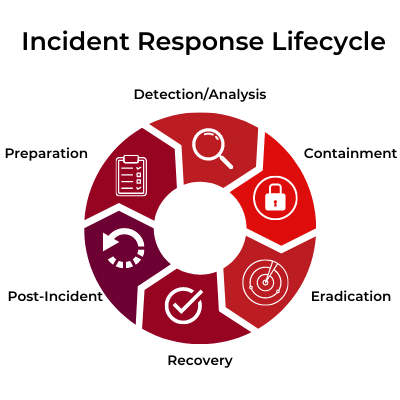
Disruptions to business operations occur frequently and vary greatly in terms of scope and scale. Organizations should establish formal policies and procedures in order to minimize the impact of disruptions. Incident response is part of the incident management process, and can be defined as the process of detecting, analyzing, responding to, and improving from disruptive events. The goal of an incident response plan is to mitigate the impact of a disruptive event and restore normal operations.
General principles of Enterprise Incident Response:
An incident response plan establishes processes that accomplish the following:
- Detect and identify events
- Triage and analyze events to determine whether an incident is underway
- Respond and recover from an incident
- Improve the organization’s capabilities for responding to a future incident.
Additionally, an effective Incident response program will accomplish the following:
- Establishment of a formal incident response plan
- Development of procedures for performing incident handling and reporting
- Establishment of guidelines for communication with outside parties
- Establishment of a team structure and staffing model
- Establishment of relationships and communication channels between the incident response team and other relevant groups
- Identification of what resources the incident response team should be provisioned with
- Staffing and training of the incident response team
Incident Response Planning Phases:
1.) Create the Incident Response Plan:
- Obtain support for Incident Response (IR) planning
- Establish event detection process
- Establish an event analysis process
- Establish and incident declaration process
- Establish incident response and recovery process
- Establish IR communication process
- Establish post IR improvement process
- Assign IR roles and responsibilities
- Review and update IR plan
2.) Test the Incident Response Plan:
- Establish the testing process
- Test the incident management plan
- Report and record the results
3.) Refine the Incident Response Pan:
- Identify criteria for revision and improvement
- Conduct post-action analysis of IR plan activities
Events and Incidents:
An event can be defined as one or more occurrences of something that affect an organization’s assets and have the potential to disrupt its operations. An incident is a high-magnitude event (or series of events) that significantly effects an enterprise’s assets and requires the organization to respond to prevent (or limit) the scope of the disruption.
Information Sharing & Communication:
Incident response planning requires the establishment of formal information sharing and communication protocols.
Communication procedures and the chain-of-custody should be established between the incident response team and the organization’s relevant stakeholders as determined by management.
These procedures should also include any external parties that might need to become involved in the incident response process (e.g., law enforcement, etc.).
Organizations should dedicate specific personnel to the Incident Response team. This team structure should also recognize organizational dependencies and ensure that the team has the adequate resources and authority to accomplish their stated duties
Establishing and supporting an ongoing incident management program enables your organization to evaluate the impact of significant events that may adversely affect employees, assets, or customers. The incident management program helps to ensure that your organization can recover its mission-critical functions and meet its responsibility to its stakeholders.
References
- https://www.cisa.gov/uscert/sites/default/files/c3vp/crr_resources_guides/CRR_Resource_Guide-IM.pdf (CERT-RMM IM)
- https://csrc.nist.gov/publications/detail/sp/800-61/rev-2/final (SP-800-61_R2)
- https://www.fema.gov/sites/default/files/2020-07/fema_nims_doctrine-2017.pdf (FEMA NIMS)
- https://resources.sei.cmu.edu/asset_files/Handbook/2016_002_001_514462.pdf (CERT-RMM)
Related Blog Posts

The Levels of CMMC 2.0 Compliance
Previously, we covered a brief history of the Cybersecurity Model Maturity Certification (CMMC 2.0 Levels) and touched on a few details of what it actually is. For this entry, we will be getting deeper into the internals of CMMC to begin breaking it down into its...

What is CMMC 2.0?
At this point, especially if you ever have contracted or subcontracted with the Federal government, you have probably at least heard the letters CMMC thrown about. There may have even been a twinge of trepidation surrounding the letters. But what do these letters...
Crypto Scams and What to Look For
First, standard disclaimer that this post is opinion and we are not licensed financial professionals, nor is anything meant to be taken as official financial advice. However, we have both direct and indirect experience with cryptocurrency and would like to share our...
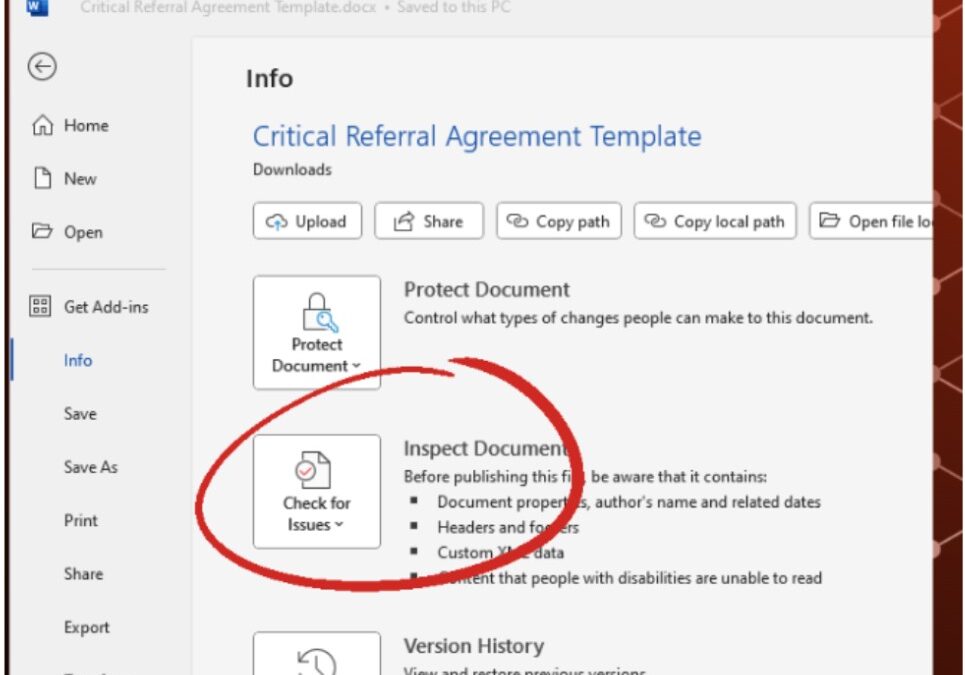
How to Remove Metadata from Word Documents
What is Metadata? According to Britannica: Metadata, data about informational aspects of other data. For example, the date and time of a text message is metadata, but the text of that message is not. The term metadata is a portmanteau of data and meta- (in the word’s...
Want to learn more? Our Security Experts Are Here For You

Newsletter
Subscribe To Our Newsletter
We've been creating some excellent webinars and local events. Join our mailing list for the latest on industry trends and strategies for cyber defense.
Need Immediate Assistance?
Give us a call (405) 771-6399
Headquarters
3841 E Danforth Rd, Ste 106, Edmond, OK 73034
110 E. Houston St, 7th Floor, San Antonio, TX 78205
Copyright 2024 - Critical Fault, LLC. | Privacy Policy